In recent discussions on why should one use a compliance and security scanner for vSphere I more than once heard a straight opinion: Why should we pay another tool. We have VUM already and just keep our vSphere cluster(s) up to date.
This opinion neglects several crucial facts about vSphere as well as any other software: Not every bug is patched once found right away. Sometimes known vulnerabilities linger for months until they are patched. In addition, some of the problems just cannot be solved by the software provider, VMware in this case.
Let me use two examples to point that out.
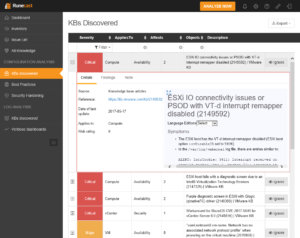
First consider being affected by this http://kb.vmware.com/kb/2149592.
It means your ESX hosts might PSOD because of a problem in the VT-d interrupt remapper. This is a known issue affecting ESXi 5.5p10, 6.0p04, 6.0u3, and 6.5.
But, there is no patch available for that. Neither a real solution. You can only circumvent the error by setting a vmkernel boot option:
esxcli system settings kernel set --setting=iovDisableIR -v FALSE
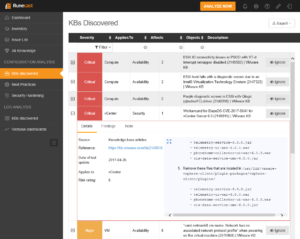
A second example would be https://kb.vmware.com/kb/2149816.
Here a remote code execution vulnerability exists in BlazeDS within vCenter 6.0 which allows an attacker to take over your vCenter server eventually.
This issue was very recently resolved in vCenter Server 6.0 U3b but was open for more than two years since the first release of 6.0.
Though an easy mitigation was possible that just implied to switch of the “Customer Experience Improvement Program” on your vCenter appliance. A telemetry phone home functionality you maybe never wanted anyways…
Remove the files located in /usr/lib/vmware-vsphere-client/plugin-packages/vsphere-client/plugins/ - telemetry-service-6.0.0.jar - telemetry-ui-war-6.0.0.war - phonehome-collector-ui-war-6.0.0.war - cis-data-service-cmc-6.0.0.jar
But how should you know of those two issues? Of course you could try to put the VMware KB under your pillow. A more effective approach would be the use of Runecast Analyzer in your environment.
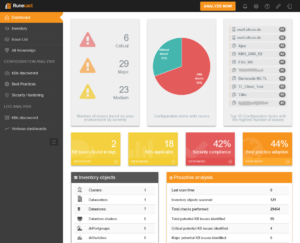
This unique and easy to use solution comes as an OVA and installs in a few minutes. Once connected to your vCenter it shows its full beauty.
Beauty lies – as always – on the side of the beholder. Here “beauty” is the worst side of your infrastructure: Its bugs, flaws and vulnerabilities.
In the web interface of Runecast Analyzer you can drill down into each issue and get a brief summary of the problem, a hyperlink to the specific KB-article as well as the necessary patch or if a mitigation is possible – e.g. if no patch is available.
You will instantly recognize these two buggers:
Runecast Analyzer has the full power of the VMware knowledgebase built in. On top of that the VMware best-practices-guides and the security-hardening-guides are checked against as well. Within seconds you get an idea of your problems as well as the solution to them.
Using the tools built-in reporting functionality, it is an easy process to regularly document the compliance level of your infrastructure and therefore also satisfy legal requirements if they apply.
A time limited trial version is available. Licensing works on the socket count of your host.
I especially like the fast installation and the almost immediate return of invest. It only takes minutes to gain a real benefit from using the tool.
Working through the list of issues of course keeps you busy – but otherwise the bad guys would be.
More information: http://www.runecast.biz.