Using vSphere-Client 6.7 to synchronize NSX-Manager with Active Directory
Once you’ve deployed NSX-Manager to a vSphere 6.7 cluster, you may have noticed an error on the dashboard.
“No NSX Managers available. Verify current user has role assigned on NSX Manager.”
Assuming you have configured vCenter connections correctly, there’s a simple explanation for the error (KB2080740).
Usually initial setup of NSX-Manager is done by the default SSO User administrator@vsphere.local. If you log into vCenter using that user, there will be no error on the dashboard. The point is that NSX-Manager has its own permissions and roles which are not coupled to vCenter permissions. That means a user with administrator rights in vCenter does not automatically get administrator rights in NSX-Manager. Without any permissions that user can’t even see NSX-Manager.
Fix it
We will now synchronize NSX-Manager with Active Directory, so we can add permissions to ADS users and groups.
Login to vSphere-Client (HTML5) with default admin (administrator@vsphere.local). Open Menu and select “Networking and Security”.
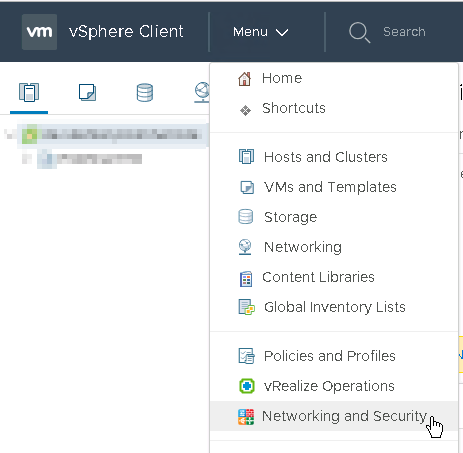
Go to System > “Users and Settings”. Menu structure has changed a little. In earlier versions of vCenter that was only available with Web-Client (Flash) and could be found at Installation > Management > NSX-Manager. Now it has moved into a section on its own, which is good.
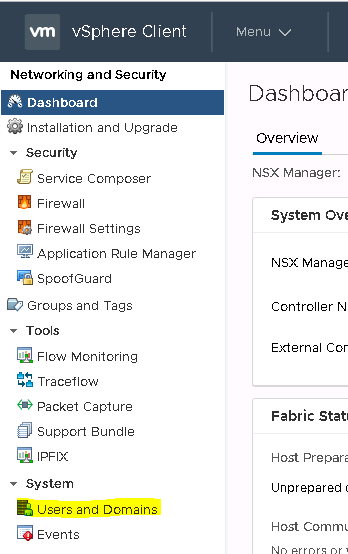
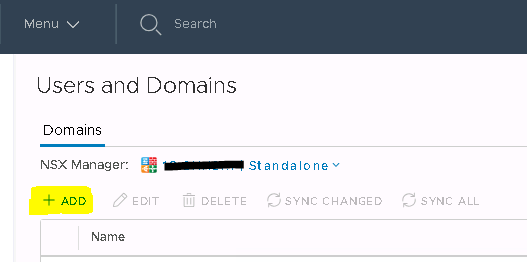
Select Domain (a user tab did not yet exist at the point of writing this article) and click “+Add”.
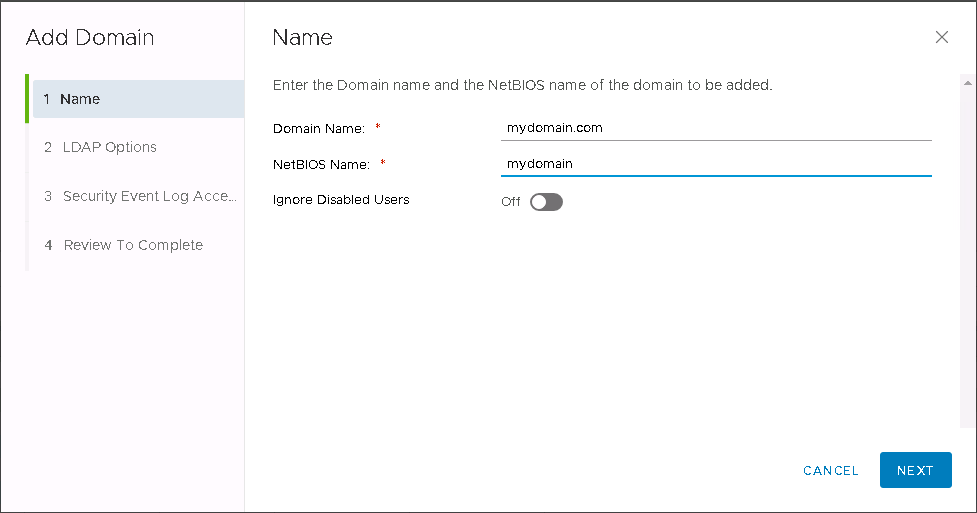
Enter your domain name and NetBIOS name. You can also opt to ignore disabled users in ADS so they will not be synchronized.
Now enter domain controller as FQDN. Protocol can either be LDAP or LDAPS. Note that modern domain controllers might refuse LDAP and require LDAPS. Default ports should work. I had some trouble with the user name until I figured out you have to enter it plain without NetBIOS name or backslash.
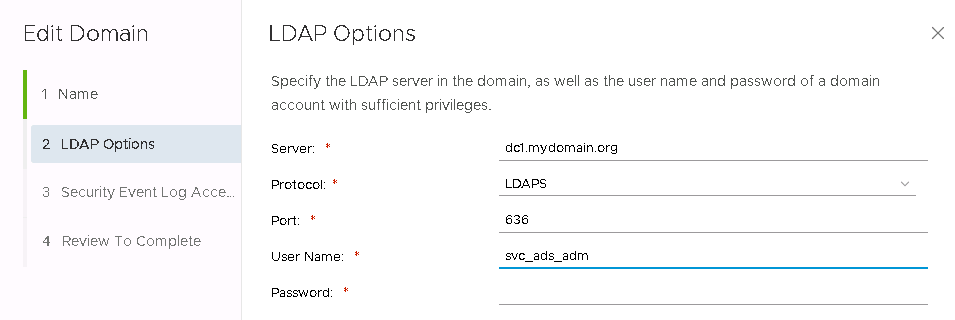
You may configure event logging to the domain controller, but that is optional.
Review your settings. If there was something wrong, you wouldn’t have come to this point. 😉
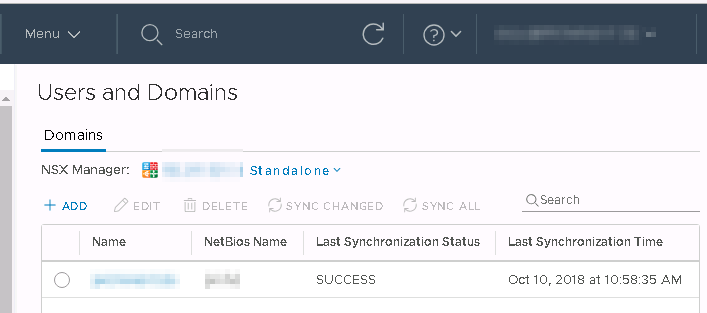
Once you click Finish you can see your configured domain on the Users and Domains page. To enforce synchronization, select your domain and click “Sync All”. Depending on the size of your ADS it can take some time.
Add Users
As you can see in the image above, there’s only a domain tab. A Users tab is still missing. Therefore we need to finish the last step in the Flashclient.
Login as administratot@vsphere.local.
Go to Home > Network and Security > System > Users and Domains
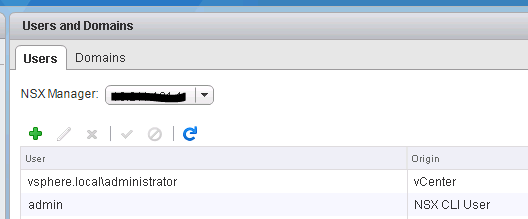
Select your NSX-Manager in the dropdown menu and click on Users tab.
Click on green + to add a user or a group.
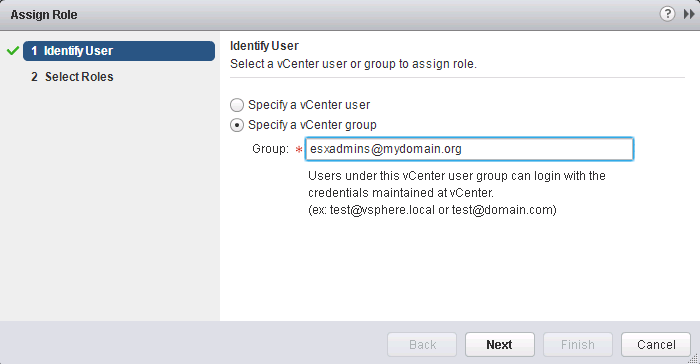
In this example we’re selecting an active directory group “esxadmins” from mydomain.org.
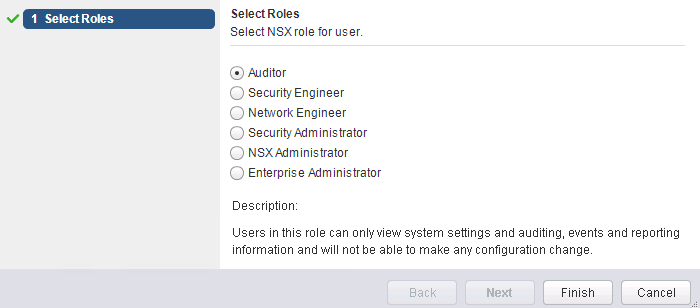
Now we need to assign a role to the group. Let’s start with Auditor, which equals “read only”. But that is enough to make the error on the vCenter dashboard disappear. Now the logged in user who is member of ADS group “esxadmins” can read details about NSX-Manager and settings.
Roles
There are two new roles to choose from. Security Engineer and Network Engineer. They’ve been introduced with NSX 6.4.2.
Enterprise Administrator: Users in this role can perform all tasks related to deployment and configuration of NSX products and administration of this NSX Manager instance.
NSX Administrator: Users in this role can perform all tasks related to deployment and administration of this NSX Manager instance. For example, install virtual appliances, configure port groups.
Security Administrator: Users in this role can configure security compliance policies in addition to viewing the reporting and auditing information in the system. For example, define distributed firewall rules, configure NAT and load balancer services.
Security Engineer: Users in this role can perform all security tasks, such as configuring policies, firewall rules. Users have read access to some networking features, but no access to host preparation and user account management.
Network Engineer: Users in this role can perform all networking tasks, such as routing, DHCP, bridging. Users have read access to endpoint security features, but no access to other security features.
Auditor: Users in this role can only view system settings, auditing, events, and reporting information and cannot make any configuration changes.
Have a look at the NSX-Administration Guide to see a full matrix of users, permissions and features.
After you’ve finished, log off and login with an ADS user who is member of a group we’ve just assigned an Auditor role. NSX-Managers and settings now should be visible and errors like “No NSX Managers available” should be gone.

