Checking the cluster’s compliance for security or hidden problems is meanwhile a standard task. There are automated tools to do the job such as VMware Skyline or Runecast Analyzer. In addition to standard vSphere clusters, the latter can also check vSAN, NSX-T, AWS, Kubernetes and, since version 5.0, Azure for compliance.
In this blog post I’d like to outline how to connect a vSphere with Tanzu [*] environment to Runcast Analyzer. [* native Kubernetes Pods and TKG on vSphere]
Some steps are simplified because it is a Lab environment. I will point this out at the given point.
Before we can register Tanzu in Runecast Analyzer, we need some information.
- IP address or FQDN of the SupervisorControlPlane
- Service account with access to the SupervisorControlPlane
- Service account access token
IP address of the Supervisor Control Plane
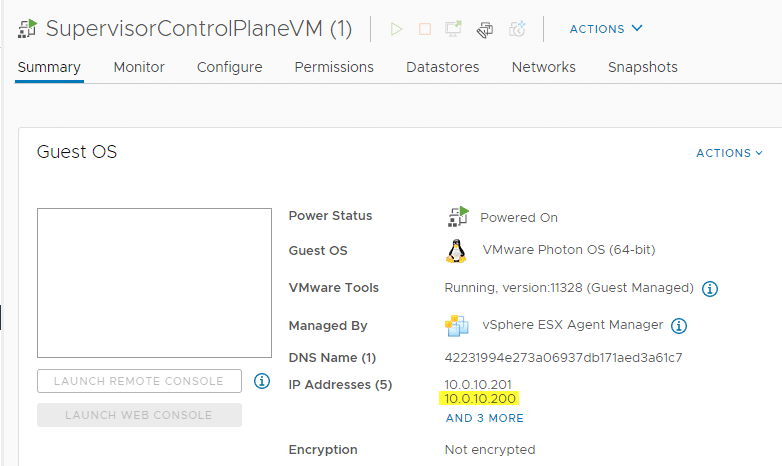
The IP address is quite easy to determine. During the rollout of the workload management, 5 consecutive IP addresses are requested. The first is the so-called Virtual IP (VIP), which is used to communicate with the ControlPlane cluster. The next three addresses are assigned to the three ControlPlane appliances and the fifth address is reserved for rolling upgrades. You can see the VIP in the vSphere client in the SupervisorControlPlane VM properties. One of the three VMs has two IP addresses in the management network. In the image below, you can see the IP of the appliance (10.0.10.201) and the VIP (10.0.10.200).
Service account
Sounds simple? Take a breath an think before you rush. 🙂
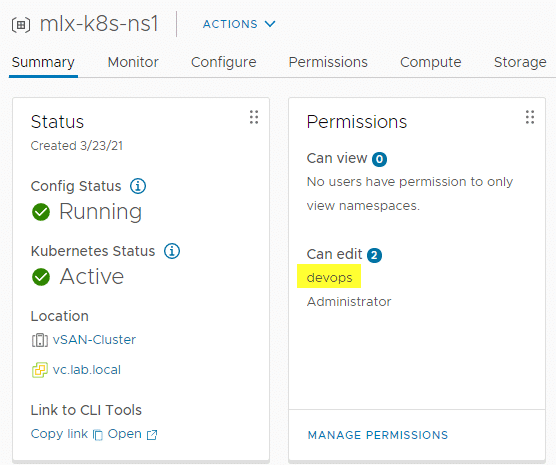
I use two local accounts in Tanzu Lab: Administrator and devops. Devops is my service account for all namespaces. Both accounts have read and write permissions to all namespaces, as you can see from the mlx-k9s-ns1 namespace shown below. However, only administrator has access to the SupervisorControlPlane! We don’t want to monitor any namespace, but the whole Tanzu cluster. Only administrator@vsphere.local has this permission. In production environments you would use a distinct service account for this too, but this is a lab.
Get the Service Account Token
We have the IP address and the service account with full access to the Tanzu cluster. Now the access token for the service account is needed. In my case it’s administrator@vsphere.local.
To do so, we open the shell of our choice with which we usually issue kubectl commands and log in to the ControlPlane. Now it is important not to use the default login ‘devops’, but administrator.
kubectl vsphere login --vsphere-username administrator@vsphere.local --server=https://10.0.10.200 --insecure-skip-tls-verify
Logged in successfully.
You have access to the following contexts:
10.0.10.200
mlx-k8s-ns1
User Administrator has access to a workspace (mlx-k8s-ns1) and the ControlPlane (10.0.10.200).
kubectl config view
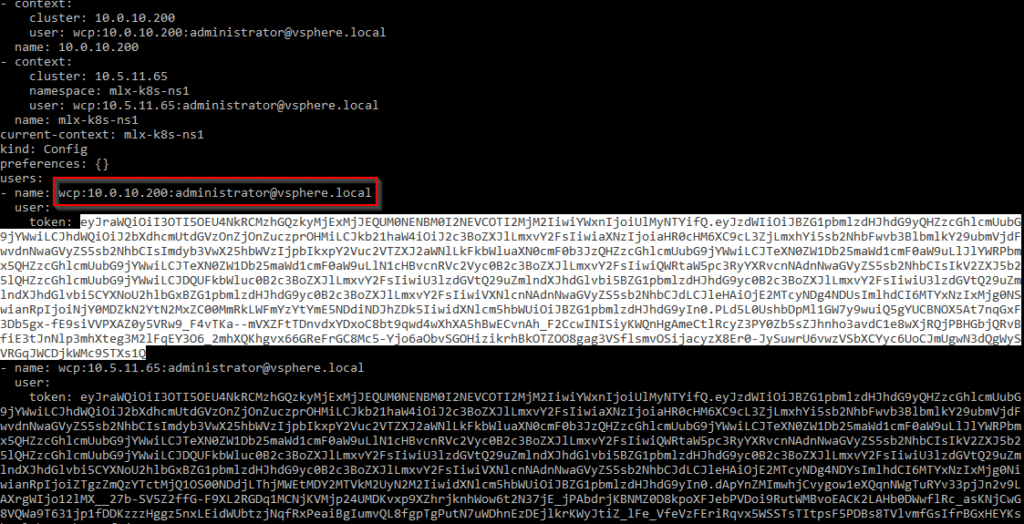
Again, we have to look carefully. We need the token which is below wcp:<ControPlane IP> :<service account> (red box). Further down is the token for accessing the namespace, which we are not interested in. We select and copy the token to the clipboard and proceed to Runecast Analyzer.
Connect K8s to Runecast
In Runecast UI we select in the upper right hand side Settings > Connections > Add Kubernetes.
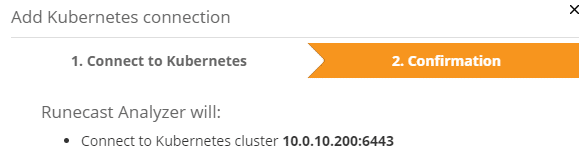
We only need the IP address of our SupervisorControlPlane and the token of the service account. The API port 6443 is default. Usually there’s no need to change it.
Copy the token from the clipboard into the text box SA token and click on [Continue].
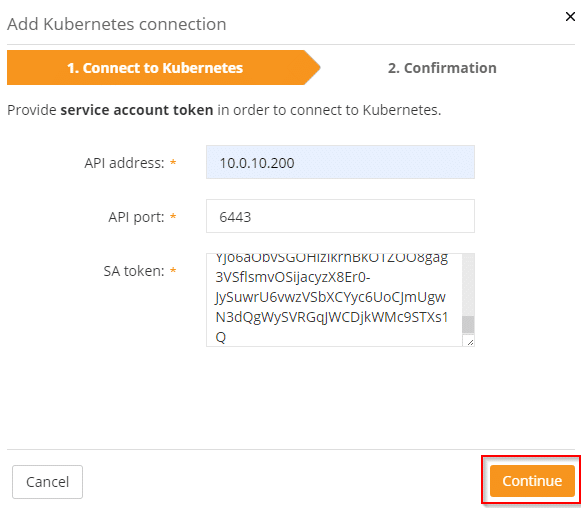
We just have to confirm the settings and Runecast will monitor our Tanzu deployment for compliance too.